[ad_1]

Getty Pictures
Researchers have unearthed by no means-prior to-observed malware that hackers from North Korea have been making use of to surreptitiously read through and down load electronic mail and attachments from contaminated users’ Gmail and AOL accounts.
The malware, dubbed SHARPEXT by scientists from security agency Volexity, takes advantage of intelligent indicates to put in a browser extension for the Chrome and Edge browsers, Volexity reported in a website submit. The extension can not be detected by the e mail services, and since the browser has already been authenticated utilizing any multifactor authentication protections in area, this increasingly well known stability measure plays no purpose in reining in the account compromise.
The malware has been in use for “perfectly about a calendar year,” Volexity claimed, and is the operate of a hacking group the firm tracks as SharpTongue. The group is sponsored by North Korea’s govt and overlaps with a team tracked as Kimsuky by other scientists. SHARPEXT is targeting organizations in the US, Europe, and South Korea that get the job done on nuclear weapons and other challenges North Korea deems important to its nationwide safety.
Volexity President Steven Adair said in an electronic mail that the extension gets installed “by way of spear phishing and social engineering exactly where the sufferer is fooled into opening a destructive document. Beforehand we have noticed DPRK danger actors launch spear phishing assaults where by the overall objective was to get the target to install a browser extension vs it remaining a write-up exploitation system for persistence and info theft.” In its existing incarnation, the malware operates only on Home windows, but Adair stated there’s no reason it couldn’t be broadened to infect browsers jogging on macOS or Linux, also.
The weblog post extra: “Volexity’s own visibility reveals the extension has been quite prosperous, as logs attained by Volexity exhibit the attacker was able to effectively steal thousands of e-mails from numerous victims by the malware’s deployment.”
Installing a browser extension through a phishing operation without the need of the end-user noticing is just not quick. SHARPEXT developers have evidently paid notice to investigation like what’s posted here, listed here, and in this article, which demonstrates how a safety mechanism in the Chromium browser motor prevents malware from generating modifications to sensitive person settings. Each individual time a legitimate adjust is manufactured, the browser requires a cryptographic hash of some of the code. At startup, the browser verifies the hashes, and if any of them will not match, the browser requests the previous options be restored.
For attackers to perform about this security, they need to 1st extract the adhering to from the personal computer they are compromising:
- A copy of the methods.pak file from the browser (which has the HMAC seed used by Chrome)
- The user’s S-ID value
- The original Preferences and Safe Tastes information from the user’s system
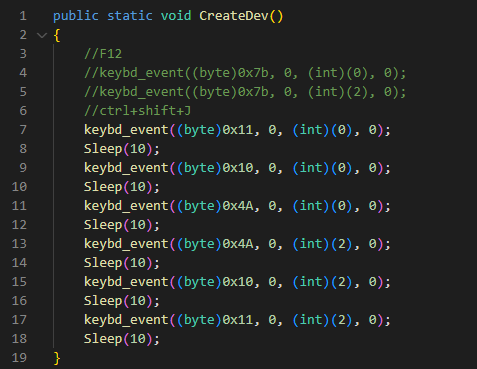
Right after modifying the choice files, SHARPEXT mechanically loads the extension and executes a PowerShell script that permits DevTools, a environment that makes it possible for the browser to run personalized code and settings.
“The script runs in an infinite loop examining for procedures connected with the targeted browsers,” Volexity discussed. “If any specific browsers are identified running, the script checks the title of the tab for a particular search term (for example’ 05101190,’ or ‘Tab+’ depending on the SHARPEXT version). The distinct key phrase is inserted into the title by the malicious extension when an active tab adjustments or when a site is loaded.”
Volexity
The write-up continued:
The keystrokes sent are equivalent to
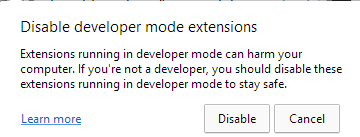
Command+Shift+J, the shortcut to permit the DevTools panel. And finally, the PowerShell script hides the newly opened DevTools window by employing the ShowWindow() API and theSW_Coverflag. At the conclude of this method, DevTools is enabled on the lively tab, but the window is concealed.In addition, this script is applied to cover any home windows that could alert the sufferer. Microsoft Edge, for example, periodically displays a warning concept to the person (Determine 5) if extensions are running in developer manner. The script continuously checks if this window appears and hides it by utilizing the
ShowWindow()and theSW_Coverflag.
Volexity
As soon as installed, the extension can complete the following requests:
| HTTP Write-up Information | Description |
| manner=list | Listing previously collected e-mail from the victim to make certain duplicates are not uploaded. This list is continuously up to date as SHARPEXT executes. |
| manner=area | Listing e-mail domains with which the victim has earlier communicated. This record is continually up to date as SHARPEXT executes. |
| manner=black | Gather a blacklist of email senders that ought to be dismissed when accumulating e-mail from the target. |
| mode=newD&d=[data] | Include a area to the checklist of all domains considered by the victim. |
| mode=attach&name=[data]&idx=[data]&body=[data] | Add a new attachment to the distant server. |
| method=new&mid=[data]&mbody=[data] | Upload Gmail details to the remote server. |
| method=attlist | Commented by the attacker receive an attachments listing to be exfiltrated. |
| mode=new_aol&mid=[data]&mbody=[data] | Upload AOL info to the distant server. |
SHARPEXT will allow the hackers to create lists of e mail addresses to overlook and to hold monitor of e mail or attachments that have already been stolen.
Volexity created the following summary of the orchestration of the many SHARPEXT parts it analyzed:

Volexity
The website publish delivers photos, file names, and other indicators that educated people today can use to ascertain if they have been targeted or infected by this malware. The firm warned that the menace it poses has grown over time and is just not probable to go absent at any time quickly.
“When Volexity initially encountered SHARPEXT, it seemed to be a tool in early advancement made up of quite a few bugs, an indication the software was immature,” the company explained. “The most up-to-date updates and ongoing servicing display the attacker is acquiring its targets, acquiring worth in continuing to refine it.”
[ad_2]
Source website link





More Stories
Entertainment – Celebrity Gossip
Talk About CCS Technology Development With China Is Good, But Not Enough Without Support From China
Business News – From Newspaper to Internet